Traceability Defined
Three Interconnected Concepts
The terms "traceability," "verifiability," and "admissibility" are often used interchangeably in security discussions, yet they represent distinct but interdependent concepts. Understanding their relationships is essential for designing and evaluating surveillance systems intended to serve as evidence.
Traceability: Reconstructing the Complete Chain
Traceability means that the complete event chain and evidence chain can be reconstructed. It is the ability to follow the path of evidence from its origin through every subsequent step until its final use. Traceability is not limited to the video itself; it encompasses the entire ecosystem surrounding the video.
A traceable surveillance system can answer these questions with documented evidence:
- Who captured this footage? What specific device, with what identity, at what location? - When was it captured? What is the precise timestamp, and how was that timestamp established and verified? - How was it transmitted? What network path did the data follow? Were there any interruptions or retransmissions? - Where was it stored? In what storage system, with what redundancy, with what protection mechanisms? - Who accessed it? Every person or system that accessed the footage, when they accessed it, what they viewed, and what actions they took. - How was it modified? Any legitimate processing (compression, format conversion, metadata addition) must be documented. - How was it extracted? When the footage was exported or retrieved for use, what was the process, and what was included in the export? - How can it be verified? What mechanisms exist to prove that the exported or presented footage matches the original?
Traceability is fundamentally about documentation and proof. A system is traceable when every step in the evidence chain is documented, logged, and verifiable.
Verifiability: Proving Authenticity and Integrity
Verifiability means we can prove that "this footage has not been tampered with and comes from a trustworthy source." Verifiability is the mechanism that makes traceability meaningful. Without verifiability, traceability documentation can itself be falsified.
A verifiable surveillance system provides mechanisms to prove:
- Source Authenticity: This footage originated from a specific, legitimate device at a specific time. - Integrity: The footage has not been modified, deleted, or corrupted since its original capture. - Completeness: All frames from the relevant time period are present; nothing has been removed or lost. - Chain of Custody: Every subsequent handling step is documented and can be proven to have occurred without tampering.
Verifiability typically relies on cryptographic mechanisms: digital signatures that prove the footage has not been modified, cryptographic hashes that can be independently verified, and time-stamping authorities that prove when footage was captured. These mechanisms transform traceability documentation from mere claims into cryptographically-proven facts.
Admissibility: Evidence That Stands Up to Challenge
Admissibility means the footage has evidential weight in disputes, audits, judicial proceedings, or arbitration. Admissibility is the ultimate goal—it is the point at which a surveillance system's evidence can actually be used to establish facts, assign responsibility, or resolve disputes.
Admissibility depends entirely on verifiability. A court, an insurance company, or a regulatory body will accept footage as evidence only if it can be proven authentic and unaltered. The burden of proof rests on the party presenting the footage. If that party cannot demonstrate verifiability, the footage will be excluded or heavily discounted.
Admissibility also depends on compliance with relevant legal and regulatory standards. Different jurisdictions have different requirements for what constitutes admissible evidence. Some require specific technical standards for video evidence. Others require documented chain of custody procedures. Some require that evidence be handled according to specific protocols to maintain admissibility.
The Relationship Between the Three Concepts
These three concepts form a hierarchy:
Traceability is the foundation. It provides the documentation and audit trail that shows what happened to the evidence. Verifiability is the mechanism. It provides the cryptographic and technical proof that the documentation is accurate and the evidence is authentic. Admissibility is the outcome. It is the point at which verified, traceable evidence can be used to establish facts and resolve disputes.A system can be traceable without being verifiable—it might have comprehensive logs, but those logs could be falsified. A system can be verifiable without being traceable—it might have cryptographic integrity protection, but no documentation of who accessed it. An admissible system must be both traceable and verifiable, and it must also comply with relevant legal and regulatory standards.
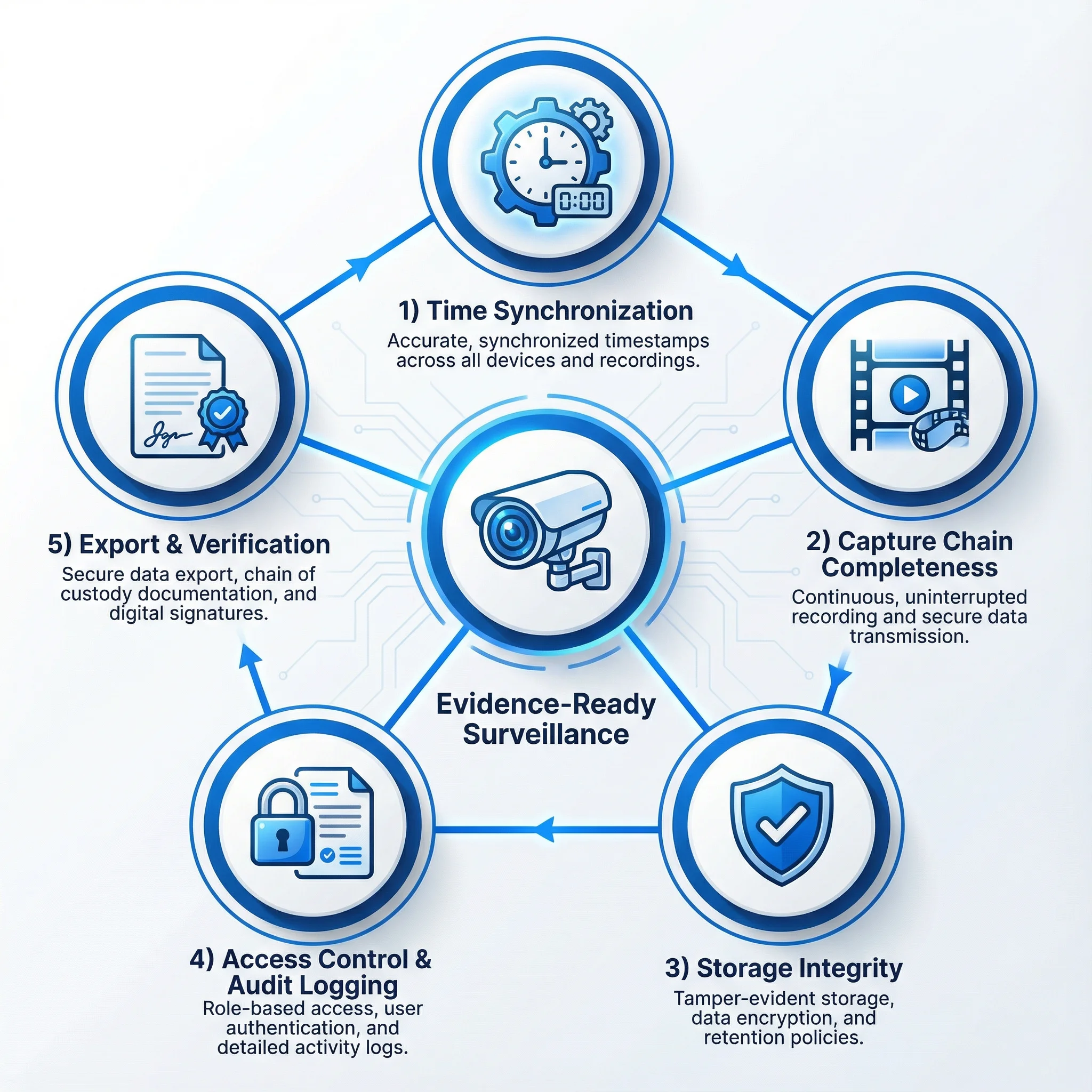
What Must Be Traceable: Beyond Just Video
The common misconception is that traceability applies only to the video file itself. In reality, a complete evidence chain requires traceability across multiple dimensions:
1. The Video Content Itself
The video file must be traceable from capture through storage through export. This includes: - Proof of the original capture device and its identity - Proof of the capture time and timezone - Proof that all frames from the relevant period are present - Proof that no frames have been added, removed, or modified - Proof of any legitimate processing (compression, format conversion)
2. The Timestamp and Time Synchronization
Timestamps are the foundation of the evidence chain. Without reliable, synchronized timestamps, the entire timeline of events becomes questionable. Traceability requires: - Proof that all devices use synchronized time (typically through NTP or similar protocols) - Documentation of time synchronization mechanisms and their accuracy - Detection and logging of any time drift or synchronization failures - Proof of the timezone and any daylight saving time adjustments - Correlation between the video timestamp and external time references (system logs, transaction records, etc.)
3. The Capture Device Identity and Status
The device that captured the footage must be identifiable and its operational status must be verifiable. Traceability requires: - Unique identification of the device (serial number, MAC address, or cryptographic identifier) - Proof of the device's location and orientation - Documentation of the device's operational status (was it functioning normally during the relevant period?) - Logs of any configuration changes, firmware updates, or maintenance - Records of the device's connectivity and any interruptions in transmission
4. The Network Path and Transmission Integrity
If footage is transmitted from the capture device to storage, the transmission path must be traceable and verifiable. Traceability requires: - Documentation of the network path (direct connection, through switches, through firewalls, through the internet) - Proof of transmission integrity (checksums, sequence numbers, retransmission logs) - Detection and logging of any packet loss or retransmission - Documentation of any encryption or compression applied during transmission - Records of any network interruptions or failover events
5. The Storage System and Access Controls
The storage system must maintain traceability of the footage and control access to it. Traceability requires: - Documentation of where footage is stored (local storage, network storage, cloud storage) - Proof of storage redundancy and backup mechanisms - Comprehensive access logs showing who accessed the footage, when, and what they did - Role-based access controls that limit who can view, export, or modify footage - Proof that storage is protected against unauthorized modification (write protection, integrity verification)
6. The Access and Modification History
Every interaction with the footage must be logged and traceable. Traceability requires: - Comprehensive audit logs of all access to the footage - Documentation of who accessed it, when, from where, and for how long - Logs of any export operations, including what was exported and by whom - Records of any legitimate processing or format conversion - Detection of any unauthorized access attempts - Proof that audit logs themselves are protected against tampering
7. The Export and Verification Process
When footage is extracted for use as evidence, the export process must be traceable and verifiable. Traceability requires: - Documentation of the export operation (who exported, when, what was exported) - Inclusion of metadata in the exported file (original capture time, device identity, storage location) - Inclusion of integrity verification in the exported file (checksums, digital signatures) - Proof that the exported file matches the original stored footage - Provision of verification tools that allow independent verification of the exported file - Documentation of the chain of custody from export through final use
The Universal Judgment Criterion
Throughout this guide, we use a single, universal criterion to evaluate whether a surveillance system is traceable and verifiable:
A surveillance system is traceable and verifiable if it can definitively answer: "Who captured this footage, when was it captured, how was it stored after capture, who accessed it and when, how was it exported, and how can we prove that the exported footage matches the original and has not been modified?"This criterion encompasses all seven dimensions above. A system that can answer all these questions with documented, verifiable evidence is evidence-ready. A system that cannot is not.
Why This Matters: The Difference Between Observation and Evidence
The distinction between traceability and mere observation is profound. An observation system answers the question: "What happened?" A traceable system answers: "What happened, and how do we know it happened that way?"
In routine operations, the difference may seem academic. When footage is reviewed for operational purposes—to understand what happened at a particular location—observation sufficiency is adequate. But the moment footage becomes evidence—when it must be used to establish facts in a dispute, investigation, or legal proceeding—traceability becomes essential.
The cost of this distinction is not merely technical. It is organizational and operational. A traceable system requires: - Synchronized time across all devices - Comprehensive logging and audit trails - Access controls and role-based permissions - Regular verification and testing - Documented procedures for export and chain of custody - Training for personnel who handle evidence - Compliance with relevant legal and regulatory standards
These requirements add complexity and cost. They are not visible in the final image quality. They do not appear in marketing materials. Yet they are the difference between a system that can be used as evidence and a system that cannot.
Looking Forward
Understanding traceability is the foundation for the remaining chapters. With this definition in place, we can examine: - The real costs when traceability is absent (Chapter 3) - The specific technical elements that enable traceability (Chapter 4) - How traceable systems compare to observation-focused systems (Chapter 5) - How to implement traceability in practice (Chapter 6) - How to verify and maintain traceability over time (Chapter 8)
The journey from "can we see it?" to "can we prove it?" begins with understanding what traceability truly means.