Implementation Roadmap and Vendor Selection
From Concept to Practice
Understanding the importance of traceability and verifiability is the first step. Implementing these concepts in a real surveillance system is the practical challenge. This chapter provides a concrete roadmap for organizations to follow when selecting, designing, deploying, and operating surveillance systems that prioritize evidence admissibility.
The Implementation Process
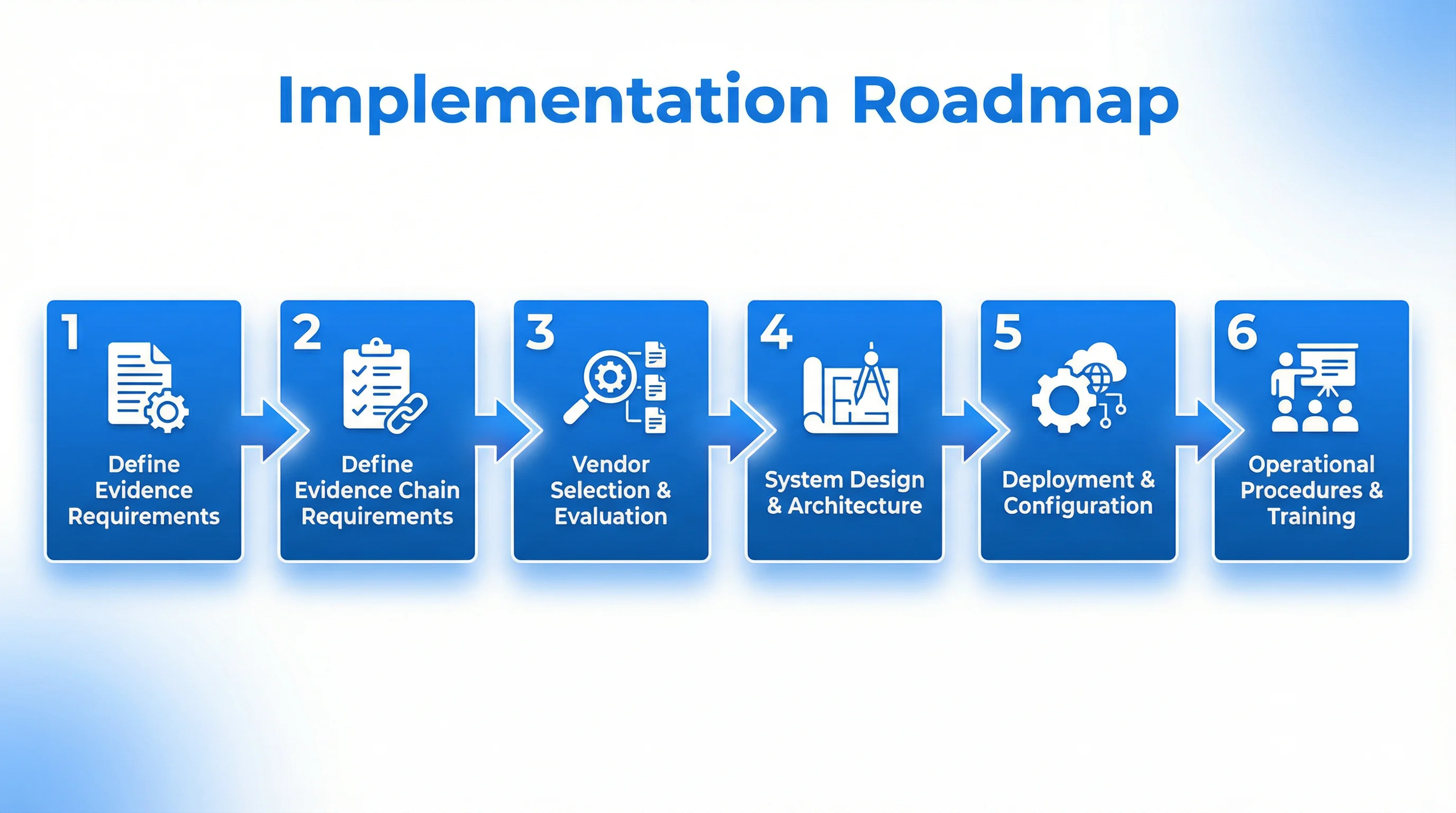
The journey from current state to evidence-ready surveillance follows a structured process. The table below outlines the six phases of implementation, with key activities, deliverables, and typical timelines for each phase.
| Phase | Key Activities | Deliverables | Timeline |
|---|---|---|---|
| Phase 1: Define Evidence Requirements | Stakeholder collaboration, incident analysis, legal/regulatory review | Evidence requirements statement, stakeholder alignment document | 2-4 weeks |
| Phase 2: Define Evidence Chain Requirements | Technical specification development for all five evidence chain dimensions | Detailed technical requirements document, acceptance criteria | 2-3 weeks |
| Phase 3: Vendor Selection and Evaluation | RFP development, vendor questionnaires, technical demonstrations, reference checks | Vendor evaluation matrix, selected vendor, contract terms | 4-8 weeks |
| Phase 4: System Design and Planning | Architecture design, infrastructure planning, integration planning, training plan | System design document, deployment plan, training materials | 3-6 weeks |
| Phase 5: Deployment and Testing | Hardware installation, software configuration, integration testing, user training | Deployed system, test results, trained users, operational procedures | 6-12 weeks |
| Phase 6: Ongoing Operations and Maintenance | Continuous monitoring, periodic verification, incident response, system updates | Operational reports, verification logs, incident documentation | Continuous |
Phase 1: Define Evidence Requirements
Before selecting or designing a system, the organization must clearly define what evidence it needs to collect and preserve. This requires collaboration among security and operations teams, legal and compliance departments, IT infrastructure staff, and finance and procurement. The output is a clear statement of evidence requirements, such as: "The organization must be able to prove that surveillance footage of access control violations is authentic, complete, and unaltered, and that all access to the footage is logged and auditable."
Phase 2: Define Evidence Chain Requirements
Based on the evidence requirements, the organization must define specific requirements for each dimension of the evidence chain. These specifications become the basis for vendor selection and system design, covering time synchronization accuracy, frame tracking mechanisms, integrity verification methods, access control policies, and export verification procedures.
Phase 3: Vendor Selection and Evaluation
With clear evidence chain requirements defined, the organization can evaluate vendors and systems. The evaluation should include technical capability assessment, detailed vendor questionnaires, proof-of-concept testing, reference checks, and cost analysis. The following table provides a vendor evaluation framework.
| Evaluation Criterion | Weight | Assessment Method | Passing Score |
|---|---|---|---|
| Time Synchronization | 20% | Technical documentation review, demonstration of NTP sync and drift detection | ≥80/100 |
| Capture Chain Completeness | 15% | Frame tracking demonstration, gap detection testing | ≥75/100 |
| Storage Integrity | 20% | Integrity verification demonstration, tamper detection testing | ≥80/100 |
| Access Control & Audit | 20% | Access control testing, audit log review, log protection verification | ≥80/100 |
| Export & Verification | 15% | Export testing, metadata review, verification tool demonstration | ≥75/100 |
| Vendor Accountability | 10% | Documentation review, certification verification, reference checks | ≥70/100 |
Vendor Questionnaire: Critical Questions
Organizations should develop a detailed questionnaire to assess vendor capabilities. The following table presents critical questions organized by evidence chain dimension.
| Dimension | Critical Questions | Required Evidence |
|---|---|---|
| Time Synchronization | How does your system synchronize time? What is the synchronization accuracy? How is time drift detected and reported? | Technical documentation, configuration examples, drift alert screenshots |
| Capture Completeness | Does your system track frame numbers? How are missing frames detected? What tools verify completeness? | Frame tracking demonstration, gap detection logs, verification tool documentation |
| Storage Integrity | What integrity verification mechanisms do you use? How frequently are checks performed? What happens when checks fail? | Integrity algorithm documentation, verification schedule, alert examples |
| Access Control | What access control mechanisms do you provide? What information is in audit logs? How are logs protected? | Access control policy examples, audit log samples, log protection documentation |
| Export Verification | What information is in exported files? Are digital signatures provided? What verification tools are available? | Export file examples, signature documentation, verification tool demonstration |
| Compliance | What legal and regulatory standards does your system comply with? Can you provide compliance documentation? | Compliance certifications, third-party audit reports, legal opinion letters |
Phase 4: System Design and Planning
With a vendor selected, the organization must design the complete system. This includes architecture design that integrates cameras, storage, networking, and time synchronization infrastructure; infrastructure planning for adequate storage capacity, network bandwidth, and processing power; integration planning with existing systems; and comprehensive training plans for all users and administrators.
Phase 5: Deployment and Testing
Deployment follows the design plan with careful attention to verification at each step. Hardware installation must be followed by configuration verification. Software configuration must be tested against the evidence chain requirements. Integration testing must verify that all components work together correctly. User training must ensure that operators understand evidence-handling procedures. Acceptance testing must confirm that all requirements are met before the system goes into production.
Phase 6: Ongoing Operations and Maintenance
Evidence-ready surveillance requires continuous operational attention. This includes daily monitoring of system health, time synchronization status, and storage integrity; weekly review of access logs and audit trails; monthly verification of integrity checksums and completeness; quarterly testing of export and verification procedures; and annual review of evidence requirements and system capabilities.
Common Implementation Challenges
Organizations implementing evidence-ready surveillance systems commonly encounter several challenges. The following table identifies these challenges and provides mitigation strategies.
| Challenge | Impact | Mitigation Strategy |
|---|---|---|
| Insufficient Budget | Cannot afford evidence-ready features, forced to compromise | Use cost calculators to demonstrate ROI, phase implementation, prioritize highest-risk areas |
| Lack of Technical Expertise | Cannot properly configure or verify evidence features | Engage external consultants, require vendor training and support, document procedures thoroughly |
| Legacy System Integration | New evidence-ready system must integrate with old systems | Plan phased replacement, use middleware for integration, document limitations of legacy components |
| Operational Resistance | Users resist new procedures and controls | Communicate evidence value clearly, provide comprehensive training, demonstrate ease of use |
| Vendor Capability Gaps | Selected vendor cannot fully meet requirements | Conduct thorough pre-selection evaluation, require proof-of-concept, include contractual guarantees |
Success Factors
Successful implementation of evidence-ready surveillance systems depends on several critical factors: executive sponsorship and budget commitment, clear evidence requirements defined upfront, thorough vendor evaluation and selection, comprehensive training for all users, ongoing operational attention and verification, and regular review and improvement of procedures. Organizations that address these factors systematically achieve evidence-ready surveillance systems that provide reliable, admissible evidence when needed.
The implementation roadmap provides a structured path from current state to evidence-ready surveillance. By following this roadmap, organizations can transform their surveillance systems from observation tools into reliable evidence platforms that withstand legal scrutiny and provide accountability when it matters most.