Case Study and Key Takeaways
A Real-World Scenario: From Crisis to Resolution
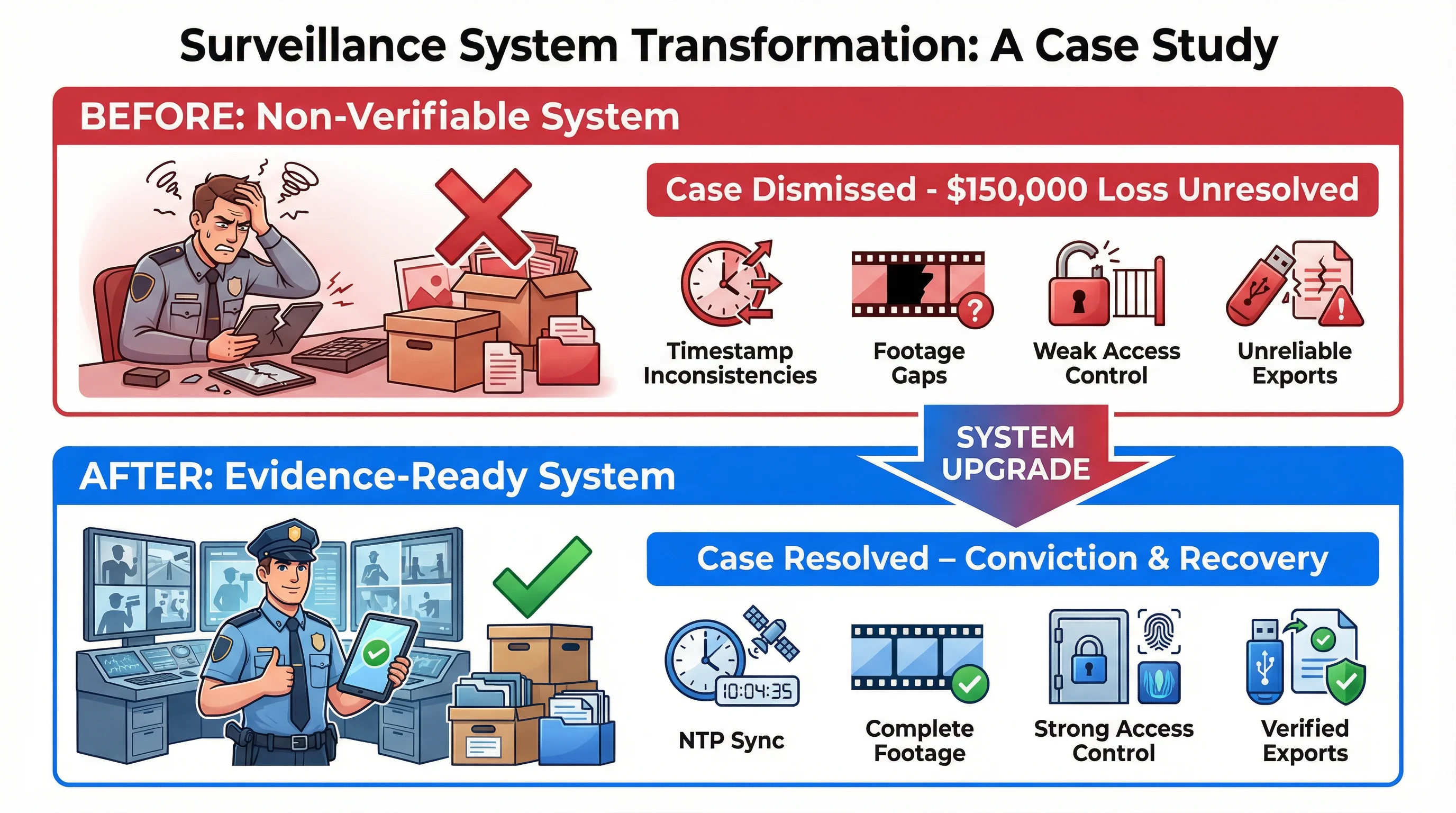
To illustrate the principles discussed throughout this guide, consider a realistic case study that demonstrates both the consequences of non-verifiable surveillance and the benefits of evidence-ready systems.
The Incident
A mid-sized logistics facility experiences a significant loss. Over a three-month period, high-value merchandise valued at approximately $150,000 has gone missing. The facility's security team suspects internal theft but lacks conclusive evidence. The facility has a surveillance system that captures clear, high-resolution footage of all areas, but the system was not designed with evidence admissibility in mind.
Initial Investigation: The Limitations of Non-Verifiable Footage
The security team reviews surveillance footage from the suspected time periods. The footage is crystal clear—the resolution is excellent, and the cameras capture fine detail. However, as the investigation progresses, several critical problems emerge:
Problem 1: Timestamp InconsistenciesThe facility's surveillance system uses local time on each device without synchronization. When the security team reviews footage from different cameras, they notice that timestamps are inconsistent. A camera on the loading dock shows an event at 14:32, while a camera in the warehouse shows the same person at 14:28. The 4-minute discrepancy raises questions: Are these the same event? Is the footage from different time periods? Without reliable timestamps, the sequence of events becomes unclear.
Problem 2: Unexplained GapsWhen reviewing footage from specific time periods, the security team discovers gaps in the recording. Footage from 13:00-13:15 on a particular day is missing from the warehouse camera. The system provides no explanation for the gap. Was there a network failure? A storage failure? A deliberate deletion? Without completeness verification, the security team cannot determine whether the gap is accidental or intentional.
Problem 3: Access Control VulnerabilitiesThe facility's surveillance system uses a single administrative password shared among multiple employees. Any employee with system access can view, modify, or delete footage. When the security team investigates who accessed the footage during the suspected theft period, they discover that the access logs are minimal and do not provide detailed information about what footage was accessed or what actions were taken. Multiple employees have administrative access, making it impossible to determine who, if anyone, tampered with the footage.
Problem 4: Export Reliability IssuesThe security team exports footage to provide to law enforcement. However, the exported files include no metadata, no checksums, and no verification information. When law enforcement receives the exported files, they cannot verify that the files are authentic or that they match the original stored footage. The exported files could have been edited, compressed, or altered in any number of ways.
Problem 5: Legal ChallengesThe security team identifies a suspect based on the surveillance footage and the suspect is arrested. However, when the case goes to court, the suspect's attorney challenges the admissibility of the surveillance footage. The attorney argues:
- The timestamps are unreliable and may not represent the actual time of the incident - The footage has unexplained gaps that could contain exculpatory evidence - The footage could have been modified by any employee with system access - The exported files cannot be verified as authentic or matching the original - The facility has no documented procedures for evidence handling or chain of custody
The judge, finding merit in these arguments, rules that the surveillance footage is inadmissible due to insufficient evidence of authenticity and integrity. Without the surveillance footage, the case against the suspect collapses. The suspect is released, and the theft remains unresolved.
The Upgrade: Implementing Evidence-Ready Surveillance
Recognizing the limitations of their current system, the facility decides to upgrade to an evidence-ready surveillance system. The upgrade includes:
Time Synchronization: All devices are configured to synchronize with an NTP time server. Time drift detection is enabled with alerts for any drift exceeding 5 minutes. Capture Chain Completeness: The new system includes frame number tracking and completeness verification tools. Any missing frames are detected and logged. Storage Integrity: All stored footage is protected with SHA-256 checksums. Integrity verification is performed monthly, and any integrity failures trigger alerts. Access Control: The new system implements role-based access control with multi-factor authentication. Only authorized personnel can access footage, and all access is logged in detail. Audit Logging: Comprehensive audit logs record who accessed what footage, when, for how long, and what actions they took. Audit logs are protected against modification. Export and Verification: Exported files include comprehensive metadata and digital signatures. Verification tools allow independent verification of exported files.The Resolution: Evidence That Stands Up to Scrutiny
With the new evidence-ready system in place, the facility conducts a new investigation into the theft. The investigation yields significantly different results:
Reliable Timestamps: The facility can prove that all timestamps are synchronized and accurate. The timeline of events is clear and unambiguous. Complete Footage: The facility can verify that all footage from the relevant time periods is complete and no frames are missing. The completeness verification report documents that all expected frames are present. Integrity Proof: The facility can prove that all stored footage has not been modified. Integrity verification reports document that all checksums match, indicating that the footage is authentic. Access Control Evidence: The facility can prove that only authorized personnel accessed the footage, and all access is documented. Access logs show exactly who accessed what footage and when. Verifiable Exports: When the facility exports footage for law enforcement, the exported files include metadata and digital signatures. Verification tools allow law enforcement to independently verify that the exported files are authentic and match the original stored footage. Chain of Custody Documentation: The facility provides comprehensive chain of custody documentation that proves the footage has been properly handled and protected from tampering.The Outcome
With this comprehensive evidence, the facility is able to identify the suspect and present the case to law enforcement. When the case goes to court, the suspect's attorney again challenges the admissibility of the surveillance footage. However, this time, the facility can respond to every challenge:
- Challenge: "The timestamps are unreliable." Response: The facility provides NTP synchronization documentation, time drift detection logs, and proof that all timestamps are accurate to within 1 second.
- Challenge: "The footage has gaps that could contain exculpatory evidence." Response: The facility provides completeness verification reports that document that all frames from the relevant time periods are present.
- Challenge: "The footage could have been modified." Response: The facility provides integrity verification reports with SHA-256 checksums that prove the footage has not been modified.
- Challenge: "The footage could have been tampered with by an insider." Response: The facility provides access logs that document exactly who accessed the footage and when. The logs show that only authorized personnel accessed the footage, and all access is documented.
- Challenge: "The exported files cannot be verified as authentic." Response: The facility provides digital signatures and verification tools that allow independent verification of the exported files.
The judge, finding that all challenges have been adequately addressed, rules that the surveillance footage is admissible. The evidence is presented at trial, and the suspect is convicted. The facility recovers the stolen merchandise and resolves the theft.
Key Differences: Before and After
The comparison between the two investigations illustrates the critical differences between non-verifiable and evidence-ready surveillance:
| Aspect | Non-Verifiable System | Evidence-Ready System | |--------|----------------------|----------------------| | Timestamp Reliability | Questioned by court | Proven with documentation | | Footage Completeness | Unexplained gaps | Verified complete | | Footage Integrity | Cannot be proven | Proven with checksums | | Access Control | Shared credentials, minimal logging | Role-based access, comprehensive logging | | Export Reliability | Cannot be verified | Verified with digital signatures | | Legal Admissibility | Excluded from evidence | Admitted as evidence | | Investigation Outcome | Unresolved | Resolved with conviction |
Five Essential Lessons
The case study illustrates five essential lessons that organizations must understand:
Lesson 1: Evidence Chain Integrity Is a Foundation, Not an Optional Feature
Many organizations view evidence chain mechanisms (time synchronization, integrity verification, access logging) as optional enhancements. The case study demonstrates that these mechanisms are not optional—they are foundational. Without them, surveillance footage cannot be used as evidence, regardless of how clear the image is.
Implication: Organizations must prioritize evidence chain integrity from the initial system design. Attempting to add these mechanisms after deployment is expensive and often ineffective.Lesson 2: Timestamps Are the Anchor Point of the Evidence Chain
The case study emphasizes the critical importance of reliable timestamps. Without synchronized, verifiable timestamps, the entire timeline of events becomes questionable. Every other element of the evidence chain depends on timestamps.
Implication: Organizations must implement time synchronization as a top priority. Time synchronization should be verified regularly, and any time drift should be detected and alerted immediately.Lesson 3: Access Logging Determines Credibility
The ability to prove that only authorized personnel accessed footage—and that all access is documented—is critical to establishing the credibility of the evidence. Without comprehensive access logs, any evidence can be challenged as potentially tampered with.
Implication: Organizations must implement comprehensive access logging and protect access logs against tampering. Access logs should be reviewed regularly for unusual patterns or unauthorized access.Lesson 4: Export and Verification Are the Final Link in the Evidence Chain
The case study demonstrates that even if all other evidence chain elements are in place, the exported file must be verifiable. Without verification mechanisms (checksums, digital signatures), exported files can be challenged as potentially modified.
Implication: Organizations must ensure that exported files include verification information and that verification tools are available to all parties who need to verify exported footage.Lesson 5: Evidence Chain Integrity Pays for Itself
The case study demonstrates that the investment in evidence-ready surveillance is justified by the ability to resolve disputes and recover losses. The cost of implementing evidence chain mechanisms is far less than the cost of unresolved theft or failed investigations.
Implication: Organizations should view evidence chain integrity as an investment, not a cost. The return on this investment is typically realized within 1-2 years through resolved disputes and recovered losses.Industry-Wide Implications
The lessons from this case study have implications for the entire security surveillance industry:
For Organizations: Organizations must prioritize evidence chain integrity when selecting and deploying surveillance systems. The lowest-cost system is not necessarily the best choice if it cannot serve as evidence. For Vendors: Vendors must invest in evidence chain mechanisms and educate customers about their importance. The market is gradually shifting toward evidence-ready systems, and vendors that fail to adapt will lose market share. For Regulators: Regulators should establish standards for evidence-ready surveillance systems. In some industries (gaming, financial services, healthcare), such standards are already emerging. In other industries, standards are needed. For Legal Professionals: Attorneys and judges should understand the technical requirements for evidence admissibility. As surveillance systems become more sophisticated, legal professionals must understand the mechanisms that make footage admissible.Conclusion: From Observation to Evidence
The journey from "can we see it?" to "can we prove it?" is the central theme of this guide. This journey requires understanding the importance of traceability and verifiability, implementing the five critical dimensions of the evidence chain, and maintaining these mechanisms over time.
The security surveillance industry has historically optimized for observation—the ability to see what happened. The industry is now beginning to recognize the importance of evidence—the ability to prove what happened. This shift is driven by regulatory requirements, legal precedents, and the real-world consequences of non-admissible footage.
Organizations that embrace this shift and invest in evidence-ready surveillance systems gain significant competitive advantages. They can resolve disputes quickly, establish accountability clearly, pass regulatory audits confidently, and use their surveillance systems as powerful tools for security and compliance.
Organizations that continue to optimize only for observation will find themselves increasingly unable to use their surveillance systems as evidence. The cost of this limitation—in litigation, settlements, regulatory penalties, and lost investigations—will eventually exceed the cost of implementing evidence chain mechanisms.
The Path Forward
The final message of this guide is simple: Traceability matters more than clarity. Verifiability is more valuable than resolution. Evidence is more powerful than observation.
Organizations that understand this message and act on it will transform their surveillance systems from observation tools into evidence platforms. They will gain the ability to prove what happened, establish accountability, and resolve disputes. They will move from asking "Can we see it?" to confidently answering "Yes, and we can prove it."
This is the future of security surveillance. This is the standard that organizations must meet. This is the foundation on which evidence-ready surveillance systems are built.
The investment in this foundation is not optional. The cost of not making this investment is too high. The benefits of making this investment are too great. The choice is clear: organizations must prioritize evidence chain integrity, implement verifiable surveillance systems, and establish the procedures and training necessary to maintain these systems over time.
The security surveillance industry is at a turning point. The organizations that recognize this turning point and adapt will thrive. The organizations that continue to optimize only for observation will struggle. The choice is yours.
---
Summary of Key Principles
Throughout this nine-chapter guide, several key principles have emerged:
1. Clarity is not evidence. A crystal-clear image that cannot be proven authentic is less valuable as evidence than a less clear image that can be proven authentic.
2. Evidence chain integrity is foundational. The five dimensions of the evidence chain (time credibility, capture chain completeness, storage integrity, access control and audit logging, export and verification) are not optional features but foundational requirements.
3. Timestamps are critical. Reliable, synchronized timestamps are the anchor point of the evidence chain. Without them, the entire timeline of events becomes questionable.
4. Access control and audit logging establish credibility. The ability to prove that only authorized personnel accessed footage and that all access is documented is critical to establishing the credibility of the evidence.
5. Export and verification are the final link. Even if all other evidence chain elements are in place, the exported file must be verifiable. Without verification mechanisms, exported files can be challenged as potentially modified.
6. Evidence chain integrity pays for itself. The cost of implementing evidence chain mechanisms is far less than the cost of non-admissible footage. The investment is typically recovered within 1-2 years.
7. Verification and maintenance are ongoing processes. Evidence-ready surveillance systems require continuous monitoring, testing, and improvement to ensure that they continue to meet evidence chain requirements over time.
8. Industry standards are emerging. Regulatory requirements and legal precedents are driving the development of industry standards for evidence-ready surveillance systems. Organizations should monitor these developments and align their systems with emerging standards.
9. The shift from observation to evidence is underway. The security surveillance industry is shifting from optimizing for observation to optimizing for evidence. Organizations that recognize this shift and adapt will gain competitive advantages.
10. The choice is clear. Organizations must prioritize evidence chain integrity, implement verifiable surveillance systems, and establish the procedures and training necessary to maintain these systems over time.
These principles provide the foundation for understanding why traceability matters more than clarity, and why evidence-ready surveillance systems are essential for organizations that need to prove what happened.