Comparison: Clarity vs. Credibility
The Fundamental Trade-Off
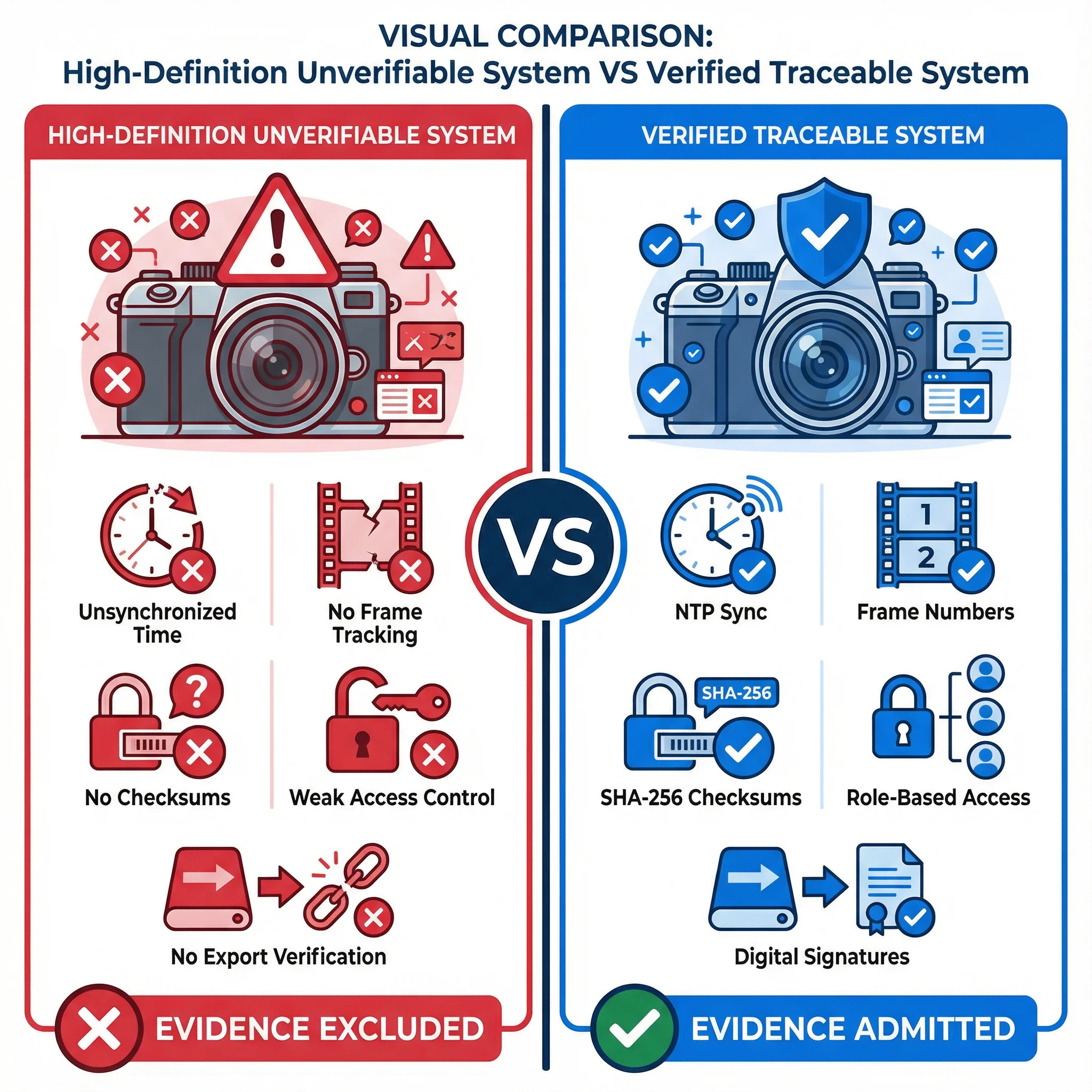
The security surveillance industry faces a fundamental choice: optimize for clarity or optimize for credibility. This chapter presents a direct comparison of two approaches: systems optimized for high-definition observation and systems optimized for evidence admissibility. The comparison reveals that clarity and credibility are not complementary—they often require different technical and operational choices.
Comparison Framework
The comparison uses seven critical dimensions that determine whether surveillance footage can be used as evidence. The table below provides a comprehensive side-by-side comparison of these two system approaches across all dimensions.
| Dimension | High-Definition, Observation-Optimized | Verified and Traceable, Evidence-Optimized |
|---|---|---|
| Time Synchronization | Local time on each device, no synchronization. Devices may have time differences of several minutes. | NTP synchronization with authoritative time source. Maximum drift: ±100ms. Continuous monitoring and alerts. |
| Continuity Proof | No frame tracking. Dropped frames are undetected. Footage may appear continuous but have gaps. | Sequential frame numbering with gap detection. Automatic logging of any discontinuity. Alerts for missing segments. |
| Storage Verification | Standard file system without integrity checksums. No mechanism to detect modifications. | Cryptographic hashes (SHA-256) for every video segment. Periodic integrity verification. Tamper detection alerts. |
| Tamper Prevention | Standard file permissions. Administrative users can modify or delete footage freely. | Write-once storage or blockchain-anchored hashes. Multi-factor authentication for sensitive operations. Role-based access control. |
| Access Audit | Basic access logs, not protected. No detailed tracking of user actions. | Comprehensive audit logs: who, what, when, how long. Logs are write-protected and backed up. Regular audit reviews. |
| Export Reliability | Standard video formats with no metadata or verification. No proof of authenticity. | Exports include metadata, digital signatures, and chain of custody documentation. Independent verification possible. |
| Vendor Accountability | No documentation of security mechanisms or evidence-handling procedures. | Detailed technical documentation. Third-party certifications. Evidence of compliance with legal standards. |
System Strengths and Weaknesses
The table above reveals fundamental differences in system design philosophy. The following analysis examines the practical implications of these differences.
High-Definition, Observation-Optimized System
Strengths: This system excels at observation. The high resolution captures fine detail. The system is simple to deploy and operate. The cost is relatively low. For applications where footage is used only for real-time monitoring or informal review, this approach is sufficient.
Weaknesses: This system is unsuitable for evidence purposes. The lack of time synchronization makes timestamps unreliable. The lack of frame tracking makes completeness unverifiable. The lack of integrity verification makes authenticity unprovable. The lack of access auditing makes tampering undetectable. The lack of export verification makes exported files challengeable.
Evidential Value: In a legal proceeding, this footage would be challenged on every dimension. The opposing party would argue that the timestamp is unreliable, frames may be missing, the footage may have been modified, unauthorized persons may have accessed it, and the exported file may not match the original. The court might exclude the footage entirely or heavily discount its reliability.
Verified and Traceable, Evidence-Optimized System
Strengths: This system is designed for evidence admissibility. Every dimension of the evidence chain is addressed. Timestamps are verifiable against authoritative sources. Frame continuity is tracked and logged. Storage integrity is cryptographically protected. Access is audited comprehensively. Exports include verification information. The vendor provides documentation and accountability.
Weaknesses: This system is more complex to deploy and operate. It requires integration with time synchronization infrastructure. It requires more sophisticated storage systems. It requires stricter access controls and audit processes. The initial cost is higher. Ongoing operational overhead is greater.
Evidential Value: In a legal proceeding, this footage is defensible. The system can provide documentation for every dimension of the evidence chain. Timestamps can be proven accurate. Frame continuity can be demonstrated. Storage integrity can be verified. Access history can be documented. Exported files can be proven authentic. The court is far more likely to admit this footage and give it full weight.
Cost-Benefit Analysis
The comparison demonstrates that evidence-optimized systems require greater investment but provide substantially greater value when footage is actually needed as evidence. The following table quantifies this trade-off.
| Factor | Observation-Optimized | Evidence-Optimized |
|---|---|---|
| Initial System Cost | Baseline | +20-40% higher |
| Operational Complexity | Low | Moderate |
| Evidence Admissibility | Questionable (30-50% chance of exclusion) | High (90%+ chance of admission) |
| Dispute Resolution Success | 50-60% of cases unresolved | 85-95% of cases resolved |
| Cost of Failed Evidence | $50,000 - $500,000 per incident | Avoided |
| ROI Timeline | N/A (no evidence value) | 1-2 successful evidence uses |
Consumer-Grade vs. Enterprise-Grade Systems
The comparison extends to different market segments. The table below contrasts consumer-grade systems typically used in small businesses with enterprise-grade verifiable systems designed for evidence purposes.
| Feature | Consumer-Grade System | Enterprise-Grade Verifiable System |
|---|---|---|
| Resolution | 1080p to 2K | 1080p to 4K (comparable) |
| Storage | Local hard drives or cloud storage without integrity verification | Redundant storage with integrity checksums, digital signatures, and write protection |
| Access Control | Simple username/password, often shared among multiple users | Multi-factor authentication, role-based access control |
| Audit Logging | Minimal or no access logging | Comprehensive access logging with protected, non-modifiable logs |
| Export Format | Standard video format, no metadata or verification | Metadata-rich exports with digital signatures and verification tools |
| Time Synchronization | Local time, no synchronization | NTP synchronization with drift detection and alerting |
| System Cost | Low ($500-$2,000 for complete system) | Higher ($5,000-$15,000 for comparable system) |
| Evidence Suitability | Inadequate for legal proceedings | Suitable for evidence purposes |
The Strategic Decision
Organizations must decide whether surveillance systems are observation tools or evidence platforms. For organizations that anticipate needing footage as evidence—in legal disputes, insurance claims, regulatory audits, or investigations—the evidence-optimized approach is justified. The incremental cost of evidence-ready features is recovered in a single successful evidence use. The cost of non-admissible footage in a critical incident far exceeds the investment in evidence integrity.
The comparison makes clear that clarity and credibility require different technical approaches. Organizations cannot assume that high-resolution footage will be admissible. They must design systems specifically for evidence purposes, with all five dimensions of the evidence chain addressed comprehensively.
The Market Failure
The security surveillance industry has historically optimized for clarity because clarity is visible and easily marketed. A 4K camera is clearly superior to a 1080p camera in terms of image detail. Vendors can demonstrate this superiority to customers. Credibility, by contrast, is not visible. A customer cannot see the difference between a system with comprehensive time synchronization and a system without it. These features only become visible when footage is needed as evidence—and by then, it is too late to retrofit them.
This market failure creates an opportunity for informed procurement. Organizations that understand the distinction between clarity and credibility can make strategic decisions that prioritize evidence-readiness. The investment in evidence-optimized systems is justified by the ability to resolve disputes, establish accountability, and avoid the substantial costs of inadmissible evidence.